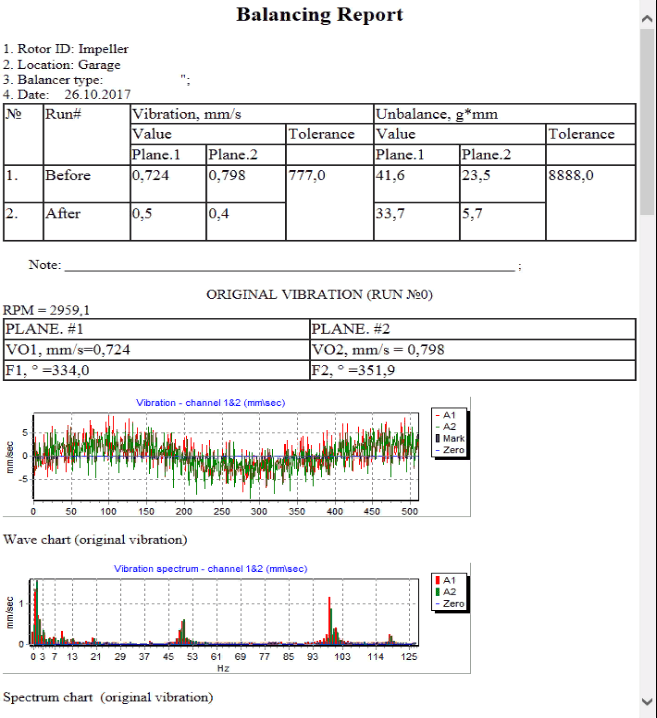
ใบเลื่อยวงเดือนสั่น? แก้ไขได้ด้วยการบาลานซ์!
เสียงดัง กึกๆ กักๆ รบกวนเวลาทำงานตัดไม้? ใบเลื่อยวงเดือนสั่นจนควบคุมยาก? ปัญหาเหล่านี้อาจเป็นสัญญาณว่าใบเลื่อยวงเดือนของคุณเสียสมดุล ซึ่งส่งผลเสียต่อคุณภาพงาน อายุการใช้งานของใบเลื่อย และที่สำคัญคือความปลอดภัยของผู้ใช้งาน

การบาลานซ์ใบเลื่อยวงเดือนเป็นสิ่งสำคัญที่หลายคนมองข้าม ใบเลื่อยที่ไม่สมดุลทำให้เกิดการสั่นสะเทือน ส่งผลให้เกิดเสียงดัง ตัดไม่เรียบ กินเนื้อไม้มากเกินความจำเป็น และอาจทำให้ใบเลื่อยแตกหักเสียหายระหว่างใช้งานได้ นอกจากนี้ การสั่นสะเทือนยังส่งผลต่อเครื่องจักร ทำให้เกิดการสึกหรอเร็วกว่าปกติอีกด้วย
ลองนึกภาพการใช้ใบเลื่อยที่คมกริบ ตัดไม้ได้อย่างราบรื่น ไม่มีเสียงดังรบกวน งานเสร็จเร็วขึ้น ประหยัดเวลา ประหยัดไม้ และที่สำคัญ ปลอดภัย ทั้งหมดนี้เป็นผลลัพธ์ที่ได้จากการบาลานซ์ใบเลื่อยวงเดือนอย่างถูกต้อง
แล้วจะทำอย่างไรให้ใบเลื่อยวงเดือนกลับมาสมดุล? Balanset-1A คือเครื่องบาลานซ์ใบเลื่อยวงเดือนที่มีความแม่นยำสูง ใช้งานง่าย และช่วยแก้ปัญหาการสั่นสะเทือนได้อย่างมีประสิทธิภาพ
Balanset-1A ออกแบบมาเพื่อให้ใช้งานได้ง่าย แม้แต่ผู้ที่ไม่มีประสบการณ์ก็สามารถเรียนรู้การใช้งานได้อย่างรวดเร็ว ด้วยระบบการวัดที่แม่นยำ Balanset-1A ช่วยระบุจุดที่เสียสมดุลบนใบเลื่อย และแนะนำวิธีการแก้ไข เพื่อให้คุณได้ใบเลื่อยที่สมดุล พร้อมใช้งานได้อย่างมีประสิทธิภาพ
หลายโรงงานและช่างไม้มืออาชีพเลือกใช้ Balanset-1A เพื่อแก้ปัญหาการสั่นสะเทือนของใบเลื่อยวงเดือน พวกเขาพบว่า Balanset-1A ช่วยลดเสียงรบกวน เพิ่มความแม่นยำในการตัด ยืดอายุการใช้งานของใบเลื่อย และที่สำคัญคือ เพิ่มความปลอดภัยในการทำงาน
ลูกค้าของเรารายหนึ่งที่เป็นเจ้าของโรงงานแปรรูปไม้ เล่าให้เราฟังว่าหลังจากใช้ Balanset-1A เสียงดังรบกวนในโรงงานลดลงอย่างเห็นได้ชัด พนักงานทำงานได้อย่างมีประสิทธิภาพมากขึ้น และที่สำคัญ ไม่มีอุบัติเหตุจากใบเลื่อยแตกหักอีกเลย
อีกรายหนึ่งเป็นช่างไม้ เขาบอกว่า Balanset-1A ช่วยให้เขาตัดไม้ได้เรียบเนียนขึ้น งานเสร็จเร็วขึ้น และลูกค้าพึงพอใจกับคุณภาพงานมากขึ้น
Balanset-1A ไม่ใช่แค่เครื่องบาลานซ์ แต่เป็นการลงทุนที่คุ้มค่า ช่วยลดต้นทุน เพิ่มประสิทธิภาพ และเพิ่มความปลอดภัยในการทำงาน ด้วยคุณภาพที่เหนือกว่า และราคาที่เหมาะสม Balanset-1A คือตัวเลือกที่ดีที่สุดสำหรับการบาลานซ์ใบเลื่อยวงเดือนของคุณ
สนใจ Balanset-1A ติดต่อเราเพื่อขอข้อมูลเพิ่มเติม และรับข้อเสนอพิเศษได้เลยวันนี้ อย่าปล่อยให้ปัญหาใบเลื่อยสั่นสะเทือน มารบกวนการทำงานและความปลอดภัยของคุณอีกต่อไป Balanset-1A พร้อมช่วยให้คุณทำงานได้อย่างราบรื่น มีประสิทธิภาพ และปลอดภัยยิ่งขึ้น
ลงทุนกับ Balanset-1A วันนี้ เพื่อผลลัพธ์ที่ดีกว่าในวันข้างหน้า
เมื่อพูดถึงเกมสล็อตออนไลน์ Co168 เป็นค่ายเกมที่มีความน่าสนใจ และได้รับความนิยมอย่างแพร่หลาย หนึ่งในคุณสมบัติที่สำคัญที่ทำให้ Co168 โดดเด่นคือการให้บริการทดลองเล่นเกมฟรี ก่อนที่ผู้เล่นจะลงเงินจริง ซึ่งเป็นสิ่งที่ควรทำ เพื่อให้คุณสามารถประเมินเกมและเตรียมพร้อมก่อนเข้าสู่การเดิมพันจริง ในบทความนี้เราจะพาคุณมาดูว่าทำไมการทดลองเล่น Co168 ฟรีจึงสำคัญและควรทำก่อนที่คุณจะใช้เงินจริง betflix
Renovating a space can be both exciting and overwhelming. Whether you are updating a room, putting in new fixtures, or doing an entire overhaul, the process often entails a significant amount of planning, purchasing materials, and executing tasks. Time is often one of the biggest challenges in renovation projects, and finding ways to work efficiently can make a large difference. One underrated tool that can prevent both time and trouble is double-sided tape. While it could seem like a easy item, it’s incredibly versatile and might help streamline a variety of renovation tasks. Let’s discover how this unassuming tool can make a major impact in your subsequent project.
1. Perfect for Short-term Fixtures
When renovating, particularly when dealing with walls, ceilings, or floors, you may need to position and reposition materials or fixtures a number of times before securing them permanently. This is where double-sided tape comes in handy. Whether or not you’re putting in wallpaper, tiles, and even hanging pictures and artwork, double-sided tape can assist you hold things in place briefly while you adjust the final placement.
As an example, in the event you’re applying wallpaper, you can use double-sided tape to hold the sides of the wallpaper down as you smooth out the rest of the sheet. This small however efficient step implies that you won’t have to rely on another person that will help you hold things up, and you can continue working efficiently.
2. Stopping Surface Damage
Throughout a renovation, it’s simple to by accident scratch or dent surfaces while moving items or working with tools. Double-sided tape can function a protective barrier. If you’re working with delicate surfaces like wood floors, countertops, or cabinets, making use of a strip of double-sided tape to the bottom of objects like tools or furniture can prevent any unsightly damage.
For instance, when repositioning cabinets or fixtures, you’ll be able to place double-sided tape on the areas that will be in contact with the floor or wall. This small precaution will prevent scrapes and scuffs while making certain everything stays securely in place.
3. Faster Installation of Small Gadgets
Double-sided tape is perfect for securing small items or elements that don’t require the heavy-duty power of screws or nails. For instance, when installing light fixtures or mirror frames, using double-sided tape to quickly hold the fixture in place lets you focus on the fine-tuning of your set up relatively than struggling to keep everything aligned.
In some cases, you may even discover that double-sided tape is robust sufficient to hold smaller, lightweight items for good, eliminating the need for drilling or hammering altogether. This is particularly useful when working in areas where drilling into the partitions is impractical, reminiscent of in rented spaces where you wish to keep away from leaving everlasting marks.
4. Quick and Easy Installations for Trim and Molding
Putting in trim and molding could be a tricky and time-consuming task that requires precision. That you must be certain that each nook is aligned perfectly, and any miscalculations can result in costly mistakes. Double-sided tape provides a fast and simple way to secure trim and molding temporarily as you adjust the ultimate position.
Instead of holding each piece of trim in place while marking and measuring, use double-sided tape to secure it to the wall. As soon as it’s aligned accurately, you can proceed to permanently affix it using nails or glue. This approach helps you save time and keep away from the frustration of holding items up for long intervals while attempting to get them just right.
5. Easier Removal and Less Clean-Up
The most effective aspects of double-sided tape is that it’s simple to remove without leaving residue or damaging surfaces. In lots of renovation projects, you’re likely to wish to reposition items or strive different arrangements to get the look or operate just right. With double-sided tape, you may quickly remove an item and reposition it without leaving any sticky residue or causing damage to your walls or surfaces.
This is particularly useful when working with short-term options or designs that require frequent adjustments. It minimizes the period of time spent cleaning up or fixing any unintended damage caused by traditional adhesives, nails, or screws.
6. Organizing Tools and Supplies
Renovations typically contain a wide range of supplies and tools scattered across the work area. Keeping these items organized can save you a number of time, especially in case you’re working on a tight schedule. Double-sided tape might help keep sure materials in place, similar to securing a roll of painter’s tape to a ladder, keeping screws or small fasteners attached to a work surface, or even temporarily holding tools in place.
By organizing tools and materials effectively, you can reduce time spent searching for misplaced items, leading to a more efficient and productive workday.
Conclusion
Renovating a space is no small task, but with a little assist from double-sided tape, you can save time, protect your surfaces, and achieve professional outcomes with ease. Whether you’re working on momentary fixtures, securing small items, or protecting surfaces, this versatile tool can make your renovation project run more smoothly. Subsequent time you’re planning a renovation, don’t overlook this easy but highly effective tool—double-sided tape just is perhaps your new greatest friend.
If you have any questions about wherever and how to use magnetic materials, you can get hold of us at the website.
Cryptocurrency has develop into a significant force in the world of finance. From Bitcoin’s meteoric rise to Ethereum’s decentralized finance (DeFi) ecosystem, crypto gives a broad spectrum of investment opportunities. However, with hundreds of digital currencies available in the market, deciding on the precise cryptocurrency to invest in could be overwhelming. Understanding what to consider when making your investment decisions is crucial to safeguarding your funds and maximizing potential returns. This is a guide on how to decide on the proper cryptocurrency for investment.
1. Understand the Basics of Cryptocurrency
Earlier than diving into the world of cryptocurrency investment, it’s essential to understand the basics. Cryptocurrencies are digital or virtual currencies that leverage blockchain technology to ensure secure transactions. Blockchain is a decentralized system that records all transactions throughout a distributed ledger, making the cryptocurrency immune to central control or manipulation. Some cryptocurrencies, akin to Bitcoin, are mined, while others, like Ethereum, assist smart contracts, which enable decentralized applications (dApps).
2. Do Thorough Research
Step one in selecting the best cryptocurrency for investment is research. Not all cryptocurrencies are created equal, and plenty of have completely different use cases, market capitalizations, and risks associated with them. Start by reading up on the cryptocurrency you are considering. Look at its whitepaper, which is a technical document that outlines its purpose, construction, and vision. Ensure the project has a strong, clear use case and that it solves a real-world problem.
Next, consider the development team behind the cryptocurrency. A credible team with proven experience in technology and business is a good indicator of a well-thought-out project. Also, evaluate the cryptocurrency’s community. A large and active community can provide assist, innovation, and growth opportunities.
3. Assess the Market Capitalization
Market capitalization is a critical metric in evaluating any cryptocurrency. It’s calculated by multiplying the current worth of a cryptocurrency by its total supply. This helps you gauge the cryptocurrency’s market worth and rank it against other digital currencies.
Cryptocurrencies are often categorized based mostly on market capitalization:
– Giant-cap cryptocurrencies (over $10 billion) are well-established, reminiscent of Bitcoin and Ethereum.
– Mid-cap cryptocurrencies (between $1 billion and $10 billion) might have significant development potential however come with elevated risk.
– Small-cap cryptocurrencies (below $1 billion) are the riskiest but might offer substantial rewards if successful.
While large-cap cryptocurrencies like Bitcoin and Ethereum are relatively stable, mid and small-cap cryptocurrencies may offer more volatility, which might lead to higher returns or losses. Consider your risk tolerance before investing in smaller projects.
4. Consider the Technology and Innovation
Technology is on the heart of cryptocurrency, and its innovation can significantly impact the worth of the asset. Cryptocurrencies that incorporate advanced applied sciences, similar to scalability, privateness, and energy efficiency, have the potential to outperform others.
For instance, Ethereum is working on Ethereum 2.zero, an upgrade designed to make the network more scalable and energy-efficient by moving from proof-of-work (PoW) to proof-of-stake (PoS). Equally, cryptocurrencies like Cardano and Polkadot intention to solve problems related to scalability and interoperability. Keep an eye on such innovations when considering which cryptocurrency to invest in.
5. Look on the Liquidity
Liquidity refers to how simply you should buy or sell a cryptocurrency without impacting its worth too much. Cryptocurrencies with higher liquidity are easier to trade, which is important for each brief-term and long-term investors. Liquidity is determined by the amount of transactions and the number of exchanges that assist the cryptocurrency.
If a cryptocurrency has limited liquidity, it may be harder to purchase or sell massive amounts without affecting the market price. Therefore, be certain that the cryptocurrency you choose is available on reputable exchanges and has a enough level of liquidity to assist your investment needs.
6. Consider the Risk Factor
Cryptocurrency investments are highly speculative and volatile. Prices can fluctuate wildly, and there are risks of hacking, fraud, and regulatory changes. Earlier than investing, assess your risk tolerance and understand that the market is still relatively young and evolving.
Diversification is one way to manage risk. Moderately than investing all your funds in a single cryptocurrency, consider spreading your investment across several options to minimize potential losses. Additionally, consider investing only what you’ll be able to afford to lose, as the market can expertise fast and unpredictable changes.
7. Monitor Regulatory Developments
Cryptocurrencies operate in a relatively uncertain regulatory environment. Totally different nations have totally different attitudes towards digital currencies, with some embracing them while others impose strict rules and even ban them. Keeping track of those developments may help you anticipate market movements and adjust your strategy accordingly.
Regulation may also have an effect on the long-term viability of sure cryptocurrencies. For example, a crackdown on privacy coins like Monero might hurt their value, while cryptocurrencies complying with regulatory frameworks may even see elevated adoption by institutions.
Conclusion
Choosing the right cryptocurrency for investment requires careful consideration of several factors, including the technology, team, market capitalization, liquidity, risk, and regulatory environment. Always bear in mind to conduct thorough research and assess your risk tolerance before making any investment decisions. Cryptocurrencies offer tremendous development potential, however they also come with risks that you should not overlook. By making informed decisions and staying up to date on market trends, you’ll be able to improve your chances of deciding on a cryptocurrency that aligns with your investment goals.
If you have any kind of questions concerning where and ways to use https://icryptox.com/2024/08/05/crypto-security-101/, you can call us at our site.
Microsoft Azure, one of the leading cloud platforms, offers quite a lot of services that help organizations scale and manage their infrastructure. Among these services, Azure Virtual Machines (VMs) play a critical position in hosting applications, databases, and different workloads in a secure and flexible environment. Azure VMs provide a complete range of security options that protect in opposition to unauthorized access, data breaches, and malicious attacks.
In this article, we will delve into the assorted security features that Azure VMs offer, and discover how they enhance the safety of your cloud infrastructure.
1. Network Security
One of the first lines of defense for any virtual machine is its network configuration. Azure provides several tools to secure the network environment in which your VMs operate:
– Network Security Teams (NSGs): NSGs can help you define rules that control incoming and outgoing site visitors to and out of your VMs. These guidelines are based on IP addresses, ports, and protocols. By implementing NSGs, you may restrict access to your VMs and be certain that only authorized traffic can reach them.
– Azure Firewall: This is a managed, cloud-based mostly network security service that protects your Azure Virtual Network. It provides centralized control and monitoring for all visitors getting into or leaving your virtual network, enhancing the security posture of your VMs.
– Virtual Network (VNet) Peering: With VNet peering, you’ll be able to securely connect completely different virtual networks, enabling communication between Azure resources. This function permits for private communication between VMs across different areas, ensuring that sensitive data does not traverse the general public internet.
2. Identity and Access Management
Securing access to your Azure VMs is essential in preventing unauthorized customers from gaining control over your resources. Azure provides several tools to manage identity and enforce access controls:
– Azure Active Directory (AAD): AAD is a cloud-based mostly identity and access management service that ensures only authenticated users can access your Azure VMs. By integrating Azure VMs with AAD, you possibly can enforce multi-factor authentication (MFA), role-primarily based access control (RBAC), and conditional access policies to limit access to sensitive workloads.
– Function-Primarily based Access Control (RBAC): Azure means that you can assign completely different roles to users, granting them varying levels of access to resources. For instance, you may assign an administrator function to a consumer who needs full access to a VM, or a read-only position to someone who only must view VM configurations.
– Just-In-Time (JIT) VM Access: JIT access enables you to restrict the time frame during which customers can access your VMs. Instead of leaving RDP or SSH ports open all the time, you should use JIT to grant temporary access when necessary, reducing the risk of unauthorized access.
3. Encryption
Data protection is a fundamental side of any cloud infrastructure. Azure provides a number of encryption options to make sure that the data stored in your VMs is secure:
– Disk Encryption: Azure affords two types of disk encryption for VMs: Azure Disk Encryption (ADE) and Azure VM encryption. ADE encrypts the operating system (OS) and data disks of VMs using BitLocker for Windows or DM-Crypt for Linux. This ensures that data at rest is encrypted and protected from unauthorized access.
– Storage Encryption: Azure automatically encrypts data at rest in Azure Storage accounts, together with Blob Storage, Azure Files, and other data services. This ensures that data stored in your VMs’ attached disks is protected by default, even if the underlying storage is compromised.
– Encryption in Transit: Azure ensures that data transmitted between your VMs and other resources within the cloud, or externally, is encrypted utilizing protocols like TLS (Transport Layer Security). This prevents data from being intercepted or tampered with during transit.
4. Monitoring and Threat Detection
Azure provides a range of monitoring tools that help detect, reply to, and mitigate threats in opposition to your VMs:
– Azure Security Center: Azure Security Center is a unified security management system that provides security recommendations and threat intelligence. It continuously monitors your VMs for potential vulnerabilities and provides insights into how one can improve their security posture.
– Azure Sentinel: Azure Sentinel is a cloud-native Security Information and Occasion Management (SIEM) resolution that helps detect, investigate, and reply to security incidents. It provides advanced analytics and uses machine learning to establish suspicious activities that will point out a possible threat.
– Azure Monitor: This service helps track the performance and health of your VMs by collecting and analyzing logs, metrics, and diagnostic data. You may set up alerts to inform you of any uncommon behavior, resembling unauthorized access makes an attempt or system malfunctions.
5. Backup and Disaster Recovery
Guaranteeing that your data is protected towards loss attributable to unintentional deletion, hardware failure, or cyberattacks is essential. Azure provides sturdy backup and disaster recovery solutions:
– Azure Backup: This service lets you create secure backups of your Azure VMs, guaranteeing which you could quickly restore your VMs in case of data loss or corruption. Backups are encrypted, and you may configure retention policies to satisfy regulatory and enterprise requirements.
– Azure Site Recovery: This service replicates your VMs to another area or data center, providing enterprise continuity in the event of a disaster. With Azure Site Recovery, you’ll be able to quickly fail over to a secondary location and reduce downtime, ensuring that your applications stay available.
Conclusion
Azure VMs are equipped with a wide array of security options that make sure the safety of your infrastructure in the cloud. From network security to identity and access management, encryption, monitoring, and disaster recovery, these tools are designed to protect your VMs towards a variety of threats. By leveraging these security capabilities, you can confidently deploy and manage your applications in Azure, knowing that your data and resources are well-protected.
If you have any sort of concerns pertaining to where and the best ways to make use of Azure Instance, you can contact us at our own web site.
Cryptocurrencies have turn into an more and more popular way to invest, trade, and store value. Nonetheless, as digital assets, they require a special kind of security compared to traditional forms of money. One of the primary tools for securing cryptocurrencies is a cryptocurrency wallet. On the planet of crypto, wallets are available in two fundamental types: hot wallets and cold wallets. Each serve the same purpose—storing your private keys (which provide you with access to your cryptocurrency)—but they do so in very different ways. Understanding the differences between these types of storage is essential for guaranteeing the safety of your digital assets.
What is a Cryptocurrency Wallet?
A cryptocurrency wallet is a software or hardware resolution that allows users to store and manage their cryptocurrencies. Quite than physically holding coins or bills, cryptocurrency wallets store private keys—the cryptographic keys that permit you to access, send, and obtain digital currencies. These private keys are the essence of cryptocurrency ownership, as anyone who possesses them can control the related funds.
While wallets don’t actually store the cryptocurrencies themselves (since cryptocurrencies are decentralized and exist on the blockchain), they facilitate the process of managing them securely.
Hot Wallets: Comfort at a Cost
Hot wallets are cryptocurrency wallets which are linked to the internet. These wallets are typically offered as apps, web-based mostly platforms, or desktop software, and so they permit users to access their funds quickly and easily from anywhere. Probably the most significant advantage of hot wallets is their convenience—you may access your crypto holdings in seconds, which is ideal for active traders or those who usually make transactions.
Because hot wallets are always online, they’re vulnerable to hacking, phishing attacks, malware, and different forms of cyber threats. When your wallet is linked to the internet, it is more vulnerable to attacks by malicious actors seeking to steal your private keys. This makes hot wallets best suited for smaller quantities of cryptocurrency that you plan to make use of in the quick term.
Types of Hot Wallets:
– Software Wallets: These could be downloaded to your pc or smartphone. Popular options embody Exodus, Electrum, and Mycelium.
– Web Wallets: These wallets are accessed through your browser, making them convenient but also vulnerable. Examples include Coinbase Wallet and MetaMask.
– Mobile Wallets: Apps like Trust Wallet or the mobile versions of desktop software wallets fall under this category.
Cold Wallets: Security First
In contrast to hot wallets, cold wallets are wallets that are not related to the internet. The term “cold” refers to the fact that these wallets are offline, which makes them much more secure than hot wallets. Cold wallets are perfect for long-term storage of cryptocurrency or for users who don’t have to access their funds frequently.
Since cold wallets are offline, they are far less vulnerable to hacking, phishing, and malware attacks. This makes cold storage particularly attractive for large-scale investors, institutional investors, or anybody looking to store a significant quantity of cryptocurrency without worrying about online security threats.
Types of Cold Wallets:
– Hardware Wallets: These are physical units, reminiscent of USB sticks, that store your private keys offline. They are portable and are available with security options like PIN protection. Standard hardware wallets embody the Ledger Nano S, Ledger Nano X, and Trezor.
– Paper Wallets: A paper wallet is a piece of paper with your private and public keys printed on it. It’s a highly secure form of storage because it’s utterly offline and can’t be hacked. Nevertheless, it requires careful dealing with to avoid losing or damaging the paper.
Evaluating Hot and Cold Wallets
1. Security:
– Hot Wallets: Handy but vulnerable to on-line threats. They are suitable for smaller quantities or funds you propose to access frequently.
– Cold Wallets: Extraordinarily secure, as they are offline. Ultimate for long-term storage of enormous amounts of crypto.
2. Ease of Use:
– Hot Wallets: Extraordinarily consumer-friendly and excellent for people who have to access their crypto quickly and make frequent transactions.
– Cold Wallets: Slightly more difficult, particularly hardware wallets, which require a number of further steps to set up and use. Nonetheless, their security benefits far outweigh the slight inconvenience.
3. Accessibility:
– Hot Wallets: Provide simple and fast access to your funds from any gadget with an internet connection.
– Cold Wallets: Not as readily accessible as hot wallets, as you should physically join the device (or access the paper wallet), however they provide peace of mind when it involves security.
Conclusion
Choosing between hot and cold wallets depends in your needs. In case you’re a frequent trader or need quick access to your funds, a hot wallet is likely the precise choice. Then again, if you happen to’re a long-term investor or wish to ensure the highest level of security to your holdings, a cold wallet is the safer option.
Many crypto customers use a mixture of both: hot wallets for everyday transactions and cold wallets for bigger quantities that they plan to hold for the long term. Regardless of which type you choose, it’s essential to understand the trade-off between convenience and security. By selecting the suitable wallet on your needs, you may help protect your digital assets from potential threats while enjoying the benefits of cryptocurrency.
If you adored this article and you would like to get more facts concerning https://icryptox.com/ kindly check out the web-page.
Cryptocurrency has revolutionized the monetary panorama, providing customers a decentralized and secure way to switch and store money. However, with nice freedom comes great responsibility. Because the popularity of digital currencies grows, so does the risk of theft and cyberattacks. Protecting your cryptocurrency is essential, especially for learners who will not be acquainted with the potential risks lurking within the digital space. In this article, we’ll break down some essential tips on the best way to secure your cryptocurrency holdings, making certain your assets stay safe.
1. Understand the Risks
Before diving into security measures, it’s essential to understand the risks involved. Cryptocurrency operates on decentralized networks, which means there is no such thing as a central authority or bank overseeing transactions. While this is a major advantage, it also signifies that if your funds are stolen, there may be little recourse. Hackers, scammers, and phishing attacks are rampant, and digital wallets are often targeted by malicious actors. Thus, safeguarding your cryptocurrency requires vigilance and the suitable security practices.
2. Use Sturdy Passwords and Two-Factor Authentication (2FA)
One of many simplest and best ways to secure your cryptocurrency is through the use of robust, unique passwords for all your accounts. A strong password ought to embrace a mixture of uppercase and lowercase letters, numbers, and symbols. Avoid utilizing easily guessable information such as birthdays or widespread words.
your password and a one-time code sent to your phone or email. This makes it significantly harder for hackers to access your accounts, even if they have your password.
3. Select the Right Wallet
hot wallets and cold wallets.
– Hot Wallets are linked to the internet and are convenient for everyday use. However, because they are always on-line, they are more susceptible to hacking.
– Cold Wallets, then again, are offline storage devices equivalent to hardware wallets or paper wallets. These are considered a lot safer because they don’t seem to be related to the internet, making them less vulnerable to online threats.
For long-term storage or massive sums of cryptocurrency, consider utilizing a cold wallet. Hot wallets, while handy, ought to only be used for smaller amounts of crypto that you simply actively trade or use.
4. Backup Your Private Keys
Your private keys are essentially the keys to your cryptocurrency. Losing them means losing access to your assets. It is crucial to back up your private keys and store them securely. Don’t store your private keys in digital form in your laptop or on-line, as this increases the risk of them being hacked.
Instead, store your private keys offline in a secure location. You need to use a USB drive, hardware wallet, or even write them down on paper and keep them in a safe place. Always ensure you have got a number of backups in case of physical damage or loss.
5. Beware of Phishing Scams
Phishing is one of the commonest ways hackers steal cryptocurrencies. This methodology includes tricking you into revealing your personal information, resembling login credentials or private keys, through fake emails or websites.
Always be cautious when receiving unsolicited emails, especially these claiming to be from cryptocurrency exchanges or wallet providers. Make sure that the website you’re visiting is legitimate by checking the URL and verifying that the site uses HTTPS encryption. By no means click on suspicious links or download attachments from untrusted sources.
6. Use a VPN for Added Protection
A Virtual Private Network (VPN) helps protect your internet connection by encrypting your data and masking your IP address. This is very vital when accessing your cryptocurrency accounts on public Wi-Fi networks, which could be insecure and prone to cyberattacks.
A VPN adds an extra layer of security by ensuring that your online activities are nameless and encrypted, reducing the chances of someone intercepting your sensitive information.
7. Keep Your Software and Units Up to date
Cybercriminals typically exploit vulnerabilities in outdated software to gain access to systems. To reduce the risk of an attack, make positive to keep all of your devices, together with computer systems, smartphones, and cryptocurrency wallet apps, up to date. Regular updates typically embody security patches that fix known vulnerabilities, making it harder for hackers to infiltrate your system.
Additionally, ensure that your antivirus software is active and updated to protect against malware and other malicious threats.
8. Consider Multi-Signature Wallets
For added security, especially for these holding large quantities of cryptocurrency, consider using multi-signature wallets. These wallets require multiple private keys to authorize a transaction, adding an additional layer of protection. This implies that even when one key is compromised, an attacker would still need access to the other keys to move your funds.
Conclusion
Protecting your cryptocurrency is essential to ensuring the safety of your assets. By following these security best practices—comparable to using strong passwords, enabling two-factor authentication, choosing the right wallet, and being cautious of phishing attacks—you can significantly reduce the risk of theft or loss. As the world of cryptocurrency continues to evolve, staying informed and vigilant is the key to securing your digital wealth.
//icryptox.com/">https://icryptox.com/2024/08/05/crypto-future-101/ kindly visit our own web-page.
When managing virtual machines (VMs) in Microsoft Azure, making certain the security and availability of your data is crucial. Azure provides varied tools to help back up your VMs and recover them when needed. Two of the most commonly used strategies for preserving VM state are snapshots and backup strategies. While each function protection mechanisms, they operate otherwise and are suitable for different scenarios. In this article, we will explore Azure VM snapshots and backup strategies intimately, serving to you understand how to effectively use them for VM management.
What’s an Azure VM Snapshot?
An Azure VM snapshot is some extent-in-time copy of the VM’s disk, capturing the exact state of the VM at the moment the snapshot is taken. These snapshots embrace the OS disk and data disks of the VM, but they don’t involve your entire VM infrastructure, such as the VM’s configuration and networking settings. Snapshots are primarily helpful for capturing a quick, read-only copy of the disk for eventualities like testing, disaster recovery, or creating backups earlier than making configuration changes.
– Create a backup of a VM’s disk earlier than performing an upgrade or installing new software.
– Quickly roll back to a previous VM state after testing a change or update.
– Clone the VM to create a new one with the identical configurations.
One of the key advantages of snapshots is that they are instantaneous and require minimal resources. They are taken from the Azure storage service, that means the data is read-only until explicitly restored. However, it’s important to note that snapshots only capture the state of the disks, not the whole system configuration, comparable to VM network settings or attached resources.
Creating a Snapshot
Within the Azure portal, locate the VM you wish to snapshot.
Right here, you’ll see all disks attached to the VM, including the OS disk and any data disks.
Select the disk you wish to snapshot, and within the disk management part, click on the “Create snapshot” option.
You possibly can choose a name and storage options for the snapshot. For example, you’ll be able to specify the storage type (Standard HDD, Commonplace SSD, etc.) and whether you wish to keep the snapshot in a unique area for disaster recovery.
Once you confirm the snapshot details, Azure will take a snapshot of the disk at that time in time.
Azure Backup Strategies
While snapshots supply an instantaneous and efficient way to protect VM data, a complete backup strategy is required to protect towards numerous disaster eventualities, corresponding to hardware failure, unintended deletion, or data corruption. Azure Backup is a strong, cloud-primarily based solution designed to safeguard VMs, files, and applications.
1. Azure Backup for VMs
Azure Backup is a fully managed service that automatically backs up Azure VMs without the necessity for additional configuration or third-party tools. It works on the VM level, ensuring that all the VM, including its disk, configuration, and associated data, is backed up regularly.
Azure Backup allows you to set up automated backup schedules to make sure regular backups of your VM.
Every backup creates a recovery point you could restore from. These factors might be retained for various intervals, permitting you to recover your VM to a particular point in time.
Azure Backup presents geo-redundancy by replicating backups to a distinct Azure area, providing additional protection against region-specific disasters.
You’ll be able to restore your complete VM or specific files and folders, offering flexibility within the recovery process.
2. Azure Site Recovery (ASR)
Azure Site Recovery (ASR) provides a higher level of protection by replicating VMs to a different region or availability zone. It is primarily designed for catastrophe recovery however may also be used to provide sturdy backup capabilities. ASR means that you can replicate the complete infrastructure, including VM configuration, networking, and disks, making certain enterprise continuity within the event of an outage or disaster.
Best Practices for Backup and Snapshot Management
Azure Backup needs to be used to create computerized, recurring backups to your VMs, ensuring which you can recover your VM at any level in time.
Earlier than making significant modifications to your VM or deploying new applications, use snapshots to create quick backups. This ensures you’ll be able to roll back to a previous state if needed.
For added security, configure geo-redundant backup storage to ensure that your backups are safe, even within the case of a region-specific failure.
Periodically test your VM recovery process to verify that your backups and snapshots can be successfully restored in case of data loss or system failure.
Conclusion
Each Azure VM snapshots and backup strategies play critical roles in making certain the resilience and availability of your virtual machines. While snapshots supply a quick and efficient way to seize the state of your VM’s disk, Azure Backup and Site Recovery provide more complete, automated solutions for long-term protection and catastrophe recovery. By understanding these tools and applying them successfully, you can be certain that your Azure VMs remain secure, recoverable, and resilient within the face of potential disruptions.
//azuremarketplace.microsoft.com/en-us/marketplace/apps/supportedimagesllc1615494954880.mongodb-rocky-linux-9?tab=Overview">Azure Windows VM kindly visit the website.
Cryptocurrency has revolutionized the way individuals understand and interact with money. As the digital financial ecosystem continues to develop, it has introduced quite a few benefits, including decentralization, transparency, and ease of cross-border transactions. Nonetheless, the increasing use of blockchain technology has raised issues about privateness and the traceability of transactions. In response to those issues, privacy coins have emerged as a solution to ensure financial anonymity, offering a new way for users to protect their identity and safeguard sensitive financial data.
What Are Privacy Coins?
Privateness coins are a category of cryptocurrencies designed specifically to protect the identity and transaction particulars of their users. Unlike traditional cryptocurrencies, such as Bitcoin or Ethereum, which are constructed on public blockchains, privacy coins implement advanced cryptographic techniques to obfuscate transaction data, ensuring that the sender, recipient, and transaction amounts stay private. While Bitcoin transactions are transparent and might be traced through the blockchain, privacy coins provide enhanced privacy features that make it tough, if not impossible, to link transactions to a selected individual or address.
The Need for Privacy in Crypto
While cryptocurrencies offer a number of advantages, they also present unique challenges when it involves privacy. In a traditional monetary system, privateness is maintained by intermediaries akin to banks, which keep customer details confidential. However, cryptocurrencies operate on decentralized networks, and each transaction is recorded on a public ledger. This transparency, while beneficial for making certain accountability and preventing fraud, also can expose users to potential risks, reminiscent of identity theft or unwanted surveillance.
For instance, law enforcement businesses and third-party trackers can trace Bitcoin transactions to particular individuals by analyzing the blockchain. Though Bitcoin is usually touted as “nameless,” all transactions are permanently recorded, creating a digital path that may be followed. In some cases, this can result in individuals or organizations having their personal information exposed, leading to unwanted attention, security risks, and privateness concerns.
How Do Privacy Coins Work?
This approach, used by coins such as Monero, mixes a user’s transaction with others, making it difficult to tell apart between the real sender and the decoys. By using a “ring” of signatures, the sender’s identity is hidden within a group of attainable senders, ensuring the transaction remains anonymous.
Privateness coins like Monero and Zcash additionally use stealth addresses, which permit the recipient of a transaction to stay anonymous. A stealth address is a one-time address created for every transaction, that means that even if somebody tracks the blockchain, they can’t link the recipient’s identity to their address.
Zero-knowledge proofs (ZKPs), implemented in coins like Zcash, permit users to prove the legitimateity of a transaction without revealing any details about it. This cryptographic technique ensures that the transaction is legitimate, without exposing any private information akin to the amount being transferred, the sender’s identity, or the recipient’s address.
These methods, among others, make privateness coins a viable solution for individuals seeking to protect their monetary data and protect their anonymity in the crypto world.
Widespread Privacy Coins
Monero is one of the most widely used privacy coins and is known for its strong emphasis on transaction confidentiality. It makes use of ring signatures and stealth addresses to make sure that transactions are untraceable, making it a popular alternative for these seeking privateness in their crypto transactions.
Zcash is another popular privacy coin that makes use of zero-knowledge proofs to enable shielded transactions. Users can choose between transparent or shielded addresses, with shielded transactions providing complete privacy for both the sender and the recipient.
Although primarily known for its give attention to fast and low-cost transactions, Dash also provides a privateness function known as PrivateSend. This function makes use of a mixing process to obfuscate transaction details, providing users with enhanced privateness when transacting.
The Way forward for Privateness Coins
As privacy concerns proceed to rise within the crypto world, privateness coins are expected to play an increasingly necessary role. The growing demand for privateness in digital monetary transactions, coupled with the evolving regulatory landscape, is likely to drive the adoption of privacy coins. In particular, as governments and financial institutions start to impose stricter rules on cryptocurrency transactions, individuals may seek privacy coins as a way to protect their identity and preserve financial freedom.
Nonetheless, the use of privacy coins isn’t without controversy. Governments and regulatory our bodies have expressed concerns about the potential for privacy coins to be used for illicit activities, resembling money laundering or tax evasion. Consequently, some international locations have moved to restrict or ban using privateness coins. Despite this, privacy coins continue to gain traction among individuals who value monetary privacy and security.
Conclusion
The rise of privateness coins marks an essential shift within the cryptocurrency panorama, providing customers a way to protect their identity and preserve the confidentiality of their transactions. As considerations over privacy and surveillance grow, privateness coins are poised to develop into an important tool in ensuring monetary freedom and privacy within the digital age. While challenges remain, comparable to regulatory scrutiny and technological hurdles, the future of privateness coins looks promising, with their potential to reshape how we think about and use cryptocurrency in an increasingly transparent world.
//icryptox.com/">https://icryptox.com/2024/08/05/cryptocurrency-101/, you can call us at our own web page.


Understanding the Security Features of Azure VMs
Microsoft Azure, one of many leading cloud platforms, affords quite a lot of services that help organizations scale and manage their infrastructure. Among these services, Azure Virtual Machines (VMs) play a critical function in hosting applications, databases, and other workloads in a secure and flexible environment. Azure VMs provide a complete range of security features that protect in opposition to unauthorized access, data breaches, and malicious attacks.
In this article, we will delve into the varied security features that Azure VMs provide, and explore how they enhance the safety of your cloud infrastructure.
1. Network Security
One of many first lines of defense for any virtual machine is its network configuration. Azure provides a number of tools to secure the network environment in which your VMs operate:
– Network Security Groups (NSGs): NSGs will let you define guidelines that control incoming and outgoing visitors to and out of your VMs. These guidelines are based on IP addresses, ports, and protocols. By implementing NSGs, you may restrict access to your VMs and make sure that only authorized site visitors can attain them.
– Azure Firewall: This is a managed, cloud-based mostly network security service that protects your Azure Virtual Network. It provides centralized control and monitoring for all site visitors coming into or leaving your virtual network, enhancing the security posture of your VMs.
– Virtual Network (VNet) Peering: With VNet peering, you’ll be able to securely join completely different virtual networks, enabling communication between Azure resources. This characteristic permits for private communication between VMs throughout completely different areas, ensuring that sensitive data doesn’t traverse the general public internet.
2. Identity and Access Management
Securing access to your Azure VMs is essential in stopping unauthorized customers from gaining control over your resources. Azure provides a number of tools to manage identity and enforce access controls:
– Azure Active Directory (AAD): AAD is a cloud-based identity and access management service that ensures only authenticated customers can access your Azure VMs. By integrating Azure VMs with AAD, you’ll be able to enforce multi-factor authentication (MFA), position-based mostly access control (RBAC), and conditional access policies to restrict access to sensitive workloads.
– Position-Based Access Control (RBAC): Azure lets you assign completely different roles to customers, granting them varying levels of access to resources. For instance, you’ll be able to assign an administrator position to a person who needs full access to a VM, or a read-only function to someone who only must view VM configurations.
– Just-In-Time (JIT) VM Access: JIT access enables you to limit the time frame throughout which customers can access your VMs. Instead of leaving RDP or SSH ports open all the time, you need to use JIT to grant short-term access when vital, reducing the risk of unauthorized access.
3. Encryption
Data protection is a fundamental facet of any cloud infrastructure. Azure provides a number of encryption options to ensure that the data stored on your VMs is secure:
– Disk Encryption: Azure presents types of disk encryption for VMs: Azure Disk Encryption (ADE) and Azure VM encryption. ADE encrypts the working system (OS) and data disks of VMs utilizing BitLocker for Windows or DM-Crypt for Linux. This ensures that data at rest is encrypted and protected from unauthorized access.
– Storage Encryption: Azure automatically encrypts data at relaxation in Azure Storage accounts, including Blob Storage, Azure Files, and different data services. This ensures that data stored in your VMs’ attached disks is protected by default, even if the undermendacity storage is compromised.
– Encryption in Transit: Azure ensures that data transmitted between your VMs and other resources within the cloud, or externally, is encrypted utilizing protocols like TLS (Transport Layer Security). This prevents data from being intercepted or tampered with during transit.
4. Monitoring and Threat Detection
Azure offers a range of monitoring tools that help detect, reply to, and mitigate threats against your VMs:
– Azure Security Center: Azure Security Center is a unified security management system that provides security recommendations and menace intelligence. It continuously monitors your VMs for potential vulnerabilities and provides insights into how you can improve their security posture.
– Azure Sentinel: Azure Sentinel is a cloud-native Security Information and Event Management (SIEM) answer that helps detect, investigate, and respond to security incidents. It provides advanced analytics and makes use of machine learning to establish suspicious activities which will point out a potential threat.
– Azure Monitor: This service helps track the performance and health of your VMs by accumulating and analyzing logs, metrics, and diagnostic data. You may set up alerts to notify you of any unusual habits, equivalent to unauthorized access makes an attempt or system malfunctions.
5. Backup and Disaster Recovery
Guaranteeing that your data is protected in opposition to loss due to accidental deletion, hardware failure, or cyberattacks is essential. Azure provides sturdy backup and catastrophe recovery solutions:
– Azure Backup: This service means that you can create secure backups of your Azure VMs, ensuring which you could quickly restore your VMs in case of data loss or corruption. Backups are encrypted, and you can configure retention policies to meet regulatory and enterprise requirements.
– Azure Site Recovery: This service replicates your VMs to a different area or data center, providing enterprise continuity within the occasion of a disaster. With Azure Site Recovery, you can quickly fail over to a secondary location and minimize downtime, making certain that your applications stay available.
Conclusion
Azure VMs are equipped with a wide array of security options that make sure the safety of your infrastructure within the cloud. From network security to identity and access management, encryption, monitoring, and disaster recovery, these tools are designed to protect your VMs towards quite a lot of threats. By leveraging these security capabilities, you’ll be able to confidently deploy and manage your applications in Azure, knowing that your data and resources are well-protected.
If you have any type of questions relating to where and how to make use of Azure VM Disk Image, you could call us at our web page.